Hey there! Have you ever wondered what all the buzz about hexadecimal crypto is? In this article, we’ll dive deep into the secrets of hexadecimal crypto and unlock all its mysteries. You’ll learn what it is, how it works, and why it’s crucial in cybersecurity. So get ready to have your mind blown and become a pro at understanding hexadecimal crypto!
If you’re intrigued by encryption and want to understand the inner workings of hexadecimal crypto, you’ve come to the right place. In this article, we’ll break down the concept of hexadecimal crypto and explain how it differs from other encryption methods. We’ll discuss the importance of hexadecimal in coding and decoding sensitive information and explore its role in ensuring secure communication and data protection. So, if you’re ready to uncover the secrets and unlock the power of hexadecimal crypto, let’s get started!

Understanding Hexadecimal Crypto
Hex Crypto, short for Hexadecimal Crypto, is a cryptographic system that utilizes the hexadecimal number system to encode and decode data. Hexadecimal is a base-16 number system which uses 16 different symbols to represent numbers. These symbols include the digits 0-9, and the letters A – F, where A represents 10, B represents 11, and so on.
What is Hexadecimal Crypto?
Hexadecimal Crypto is a method of encrypting and decrypting data using the hexadecimal number system. It is often used in computer systems and networks for various purposes, such as secure communication, data storage, and cryptography. Hex Crypto offers a higher complexity level than other encryption methods, making it more secure against unauthorized access.
How is Hexadecimal Crypto Used?
Hexadecimal Crypto is used in many applications where data security is paramount. It is commonly used in computer programming, digital communications, and cryptographic algorithms. One main application is storing and transmitting binary data, as hexadecimal representation provides a more concise and easily readable format.
Hex Crypto is also utilized in encryption algorithms to secure sensitive information, such as passwords and financial data. Converting the data into hexadecimal form makes it much more challenging for hackers to understand and manipulate the information without possessing the necessary decryption key.
Advantages of Hexadecimal Crypto
One of the key advantages of Hex Crypto is its compact representation of binary data. Each digit in the hexadecimal number system represents four bits, allowing for a more concise representation of binary values. This makes handling and transmitting large amounts of data easier and reduces storage requirements.
Another advantage of Hex Crypto is its compatibility with computer systems and networks. Most computer systems use binary code, and hexadecimal is a convenient way to represent binary data. Hex Crypto can be easily converted to and from binary, making it suitable for various computing and digital communications applications.
Hex Crypto also offers a higher security level than other encryption methods. Using a large number base and including letters in the number system significantly increases the complexity of the encryption process. This complexity makes it more difficult for hackers to decipher the encrypted data without the correct decryption key.
Critical Concepts in Hexadecimal Crypto
Hexadecimal Number System
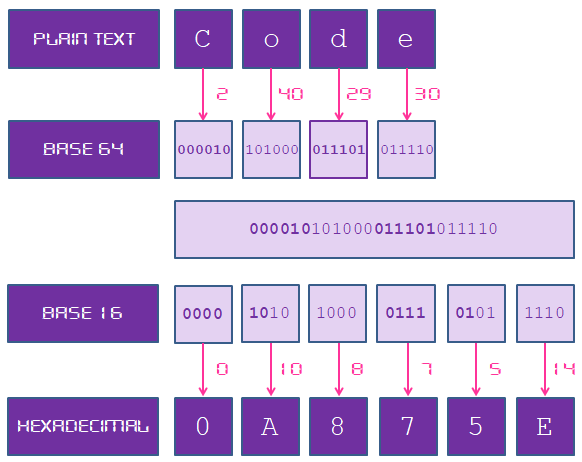
The hexadecimal number system is a base-16 number system that uses 16 different symbols to represent numbers. These symbols include the digits 0-9 and the letters A-F. In this system, each digit represents four bits of binary information, allowing for a more compact representation of binary data.
To convert a hexadecimal number to a decimal, you can use the following formula:
decimal = (digit1 * 16^3) + (digit2 * 16^2) + (digit3 * 16^1) + (digit4 * 16^0) For example, the hexadecimal number 2F can be converted to decimal as:
decimal = (2 * 16^1) + (15 * 16^0) = 47 Conversion from Hex to Binary
Converting a hexadecimal number to binary is relatively straightforward. Each hexadecimal digit can be replaced by its four-bit binary equivalent.
For example, the hexadecimal number 2F can be converted to binary as:
2 = 0010 F = 1111 So, the binary equivalent of 2F is 00101111.
Conversion from Binary to Hex
Converting a binary number to hexadecimal involves grouping the binary digits into four sets and replacing each set with its equivalent.
For example, the binary number 00101111 can be converted to hexadecimal as:
0010 1111 2 F So, the hexadecimal equivalent of 00101111 is 2F.
Hexadecimal Encryption Algorithms
Overview of Hexadecimal Encryption
Hexadecimal encryption algorithms are cryptographic methods that use the hexadecimal number system to encrypt and decrypt data. These algorithms employ various techniques and mechanisms to ensure data confidentiality and protect against unauthorized access.
Hexadecimal encryption algorithms often involve symmetric or asymmetric encryption techniques, key management, and authentication protocols. These algorithms convert the plain text into hexadecimal form, making it more difficult for unauthorized individuals to access or decipher the encrypted data.
Common Hexadecimal Encryption Algorithms
There are several common hexadecimal encryption algorithms used in modern cryptography. Some of the most widely used ones include:
- AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm that uses a 128-bit block size and key sizes of 128, 192, or 256 bits. It is widely used in various applications, including securing data in networks and storage systems.
- RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm that uses a pair of keys: a public key for encryption and a private key for decryption. It is commonly used for secure communication and digital signatures.
- Blowfish: Blowfish is a symmetric encryption algorithm that operates on 64-bit blocks and allows for key sizes ranging from 32 to 448 bits. It is known for its strong security and high performance, making it suitable for various applications.
Hexadecimal Decryption Techniques
Decrypting Hexadecimal Crypto
Decrypting hexadecimal crypto involves reversing the encryption process using the appropriate decryption key. The decryption key is usually generated during the encryption process and is required to convert the encrypted hexadecimal to its original plain text form.
The decryption algorithm reverses the steps performed during encryption to decrypt a hexadecimal value. It retrieves the original binary data from the hexadecimal representation and converts it back into plain text using the appropriate conversion method.
Tools and Methods for Decryption
Various tools and methods are available for decrypting hexadecimal crypto, depending on the encryption algorithm used. Decryption tools are often provided as part of the encryption software package or as standalone applications.
One common method for decrypting hexadecimal crypto is to use dedicated decryption software that supports the specific encryption algorithm. These tools often require the input of the encrypted hexadecimal data and the decryption key, and they can provide the decrypted plain text as the output.
For advanced users and developers, it is also possible to create custom decryption algorithms using programming languages and cryptographic libraries. These custom methods allow for more flexibility and control over the decryption process but require a deeper understanding of cryptography and programming concepts.
Security Considerations in Hexadecimal Crypto
Ensuring Data Confidentiality in Hex Crypto
Data confidentiality is a crucial aspect of cryptographic systems, including Hex Crypto. To ensure data confidentiality, various security considerations must be considered.
One of the primary security measures is the selection of a strong encryption algorithm. Choosing an algorithm that is resistant to cryptographic attacks and provides high security is essential. Using industry-standard algorithms, such as AES or RSA, is often recommended.
Another aspect to consider is the secure management of encryption keys. Encryption keys are used to encrypt and decrypt the data, and their secrecy is crucial for maintaining data confidentiality. It is essential to use strong and unique keys for each encryption process and to protect them using secure storage and management practices.
Protecting against Hexadecimal Crypto Attacks
Like any other cryptographic system, Hex Crypto is vulnerable to various attacks. These attacks can exploit weaknesses in the encryption algorithm, key management, or implementation details to gain unauthorized access to the encrypted data.
To protect against cryptographic attacks, staying updated with the latest security practices and standards is crucial. This includes regularly updating encryption algorithms and protocols to address known vulnerabilities and weaknesses. Additionally, thorough testing and verification of the cryptographic implementation is essential to identify and fix potential security flaws.
Implementing secure key management practices is also crucial for protecting against attacks. This includes using strong, random keys, securely storing them, and regularly rotating them to minimize the impact of potential vital compromises.
Applications of Hexadecimal Crypto
Hex Crypto in Blockchain Technology
Hex Crypto plays a significant role in blockchain technology, the foundation of cryptocurrencies like Bitcoin and Ethereum. Blockchain relies on cryptographic techniques to ensure data integrity and security.
In blockchain systems, Hex Crypto is used to secure the transaction data and create digital signatures. Each transaction is encrypted using hashing algorithms, which generate a unique hexadecimal representation. The transactions are then added to the blockchain, creating an immutable record of the transaction history.
Hex Crypto also plays a crucial role in the consensus mechanism used in blockchain systems, such as proof-of-work and proof-of-stake. These mechanisms rely on cryptographic algorithms, including hexadecimal encryption, to validate and secure the transactions and maintain the integrity of the blockchain.
Hexadecimal Crypto in Network Security
Hex Crypto is widely used in network security to ensure data confidentiality and integrity. It is commonly used in secure protocols, such as HTTPS, which encrypt data exchanged between web browsers and web servers.
Network security protocols based on Hex Crypto use encryption algorithms to protect data from unauthorized access during transmission. The data is encrypted using the appropriate encryption key, converted into hexadecimal form, and transmitted over the network. At the receiving end, the encrypted hexadecimal data is decrypted back into its original form using the appropriate decryption key.
Hex Crypto also plays a role in secure network communications, such as virtual private networks (VPNs) and secure email protocols. These protocols use cryptographic algorithms to encrypt the data and ensure secure communication between the sender and the recipient.
Future Trends in Hexadecimal Crypto
Emerging Technologies and Hex Crypto
As technology advances, new cryptographic techniques and algorithms will likely emerge. These advancements may lead to the development of more secure and efficient encryption methods using the hexadecimal number system.
One emerging technology that could significantly impact Hex Crypto is quantum computing. Quantum computers have the potential to break many of the existing encryption algorithms, including those based on hexadecimal crypto. As a result, researchers are exploring the development of post-quantum encryption algorithms that would resist attacks by quantum computers.
Potential Innovations in Hexadecimal Crypto
Innovation in Hex Crypto may come from improved encryption algorithms and techniques. Developing more efficient and secure algorithms could enhance the performance and reliability of hexadecimal cryptosystems.
Another potential innovation is integrating artificial intelligence (AI) and machine learning (ML) into cryptographic systems. AI and ML algorithms can be used to analyze and identify potential security vulnerabilities in cryptographic systems and improve their overall security.
Challenges in Hexadecimal Crypto
Addressing Key Challenges in Hex Crypto Implementation
One of the key challenges in Hex Crypto implementation is the complexity of the hexadecimal number system. The inclusion of letters in the number system adds layer of complexity, which can make it more challenging to understand and work with hexadecimal data.
Another challenge is ensuring compatibility between different computer systems and networks. Hex Crypto systems need to be able to convert between different number systems, such as hexadecimal and binary, to allow for seamless integration between various components.
Improving Performance and Scalability of Hex Crypto
Another challenge in Hex Crypto is the performance and scalability of cryptographic algorithms. As the volume of encrypted and decrypted data increases, the computational requirements can become a bottleneck. Improving the performance and scalability of Hex Crypto algorithms is essential for their widespread adoption and use in various applications.
Efforts are being made to develop more efficient encryption algorithms and hardware acceleration techniques to improve the performance of Hex Cryptosystems. These advancements aim to make encryption and decryption processes faster and more scalable, allowing for secure communication and data storage at higher speeds and volumes.
Legal and Ethical Considerations in Hex Crypto
Regulatory Considerations in Hex Crypto Usage
The use of cryptographic techniques, including Hex Crypto, is subject to various regulations and laws in different jurisdictions. Governments and regulatory bodies often impose restrictions on using and exporting cryptographic algorithms and products to prevent misuse and maintain national security.
Individuals and organizations must ensure compliance with relevant regulations and laws when using Hex Crypto. This includes obtaining the necessary licenses or approvals and following established guidelines for secure encryption practices.
Ethical Implications of Hexadecimal Crypto
Like any other technology, Hex Crypto has ethical implications that must be considered. Encryption technology can be beneficial and potentially harmful, depending on how it is used.
Hex Crypto allows individuals and organizations to protect their privacy and secure their sensitive information. It allows for secure communication, protects against identity theft, and enables secure financial transactions. However, encryption can also be misused for illegal activities, such as hacking, cyber-terrorism, and money laundering.
Individuals and organizations need to use Hex Crypto ethically and responsibly, following legal guidelines and ensuring that the technology is not used for malicious purposes.
Conclusion
Hexadecimal Crypto, or Hex Crypto, is a powerful cryptographic system that utilizes the hexadecimal number system to encrypt and decrypt data. It offers higher security and confidentiality than other encryption methods and is widely used in various applications, including computer programming, digital communications, and network security.
Understanding the key concepts and techniques in Hex Crypto is crucial for effectively implementing and using this cryptographic system. By staying updated with the latest advancements and best practices in Hex Crypto, individuals, and organizations can unlock the secrets of this powerful encryption method and protect their data in an increasingly digital world.



